UbiqOTTO – Enterprise WiFi & Apple Device Security Engineers
WiFi 7 Upgrades • Mobile Lockdown • Tactical Forensics • Outdoor Deployments
UbiqOTTO delivers advanced wireless architecture, Apple iOS device lockdowns, forensic auditing, and secure connectivity for time-sensitive or regulated environments.
Full-Site Wi-Fi 7 Upgrades in 24 Hours
We perform tri-band 6 GHz access-point swaps, OFDMA tuning, BSS coloring, and QoS optimization for high-density environments—overnight.
Temporary Outdoor Gigabit Internet
Encrypted directional mesh nodes for pop-up command centers, public events, or field ops—deployed same-day.
iOS Security & Digital Forensics
Apple Business Manager supervised MDM lockdowns, zero-trust policies, and deep forensic recovery for lost or compromised devices.
UbiqOTTO has been tracking iOS exploitations since the iPhone first replaced the Blackberry as the choice for corporate and enterprise solutions. We've been instrumental in network recovery efforts following some of the most critical iOS attacks, including early breaches like the **Trident (2016)** zero-day chain, and more recently, sophisticated campaigns leveraging **Pegasus (FORCEDENTRY, BLASTPASS)** and **Operation Triangulation (2023)**.
As of 2025, we continue to meticulously track emerging threats such as advanced zero-click vulnerabilities, new vectors in supply chain attacks targeting mobile deployments, and innovative social engineering exploits. Our dedicated iPhone and iPad forensic audits are a rapidly expanding segment of our services, providing unparalleled insights into device integrity and network resilience.
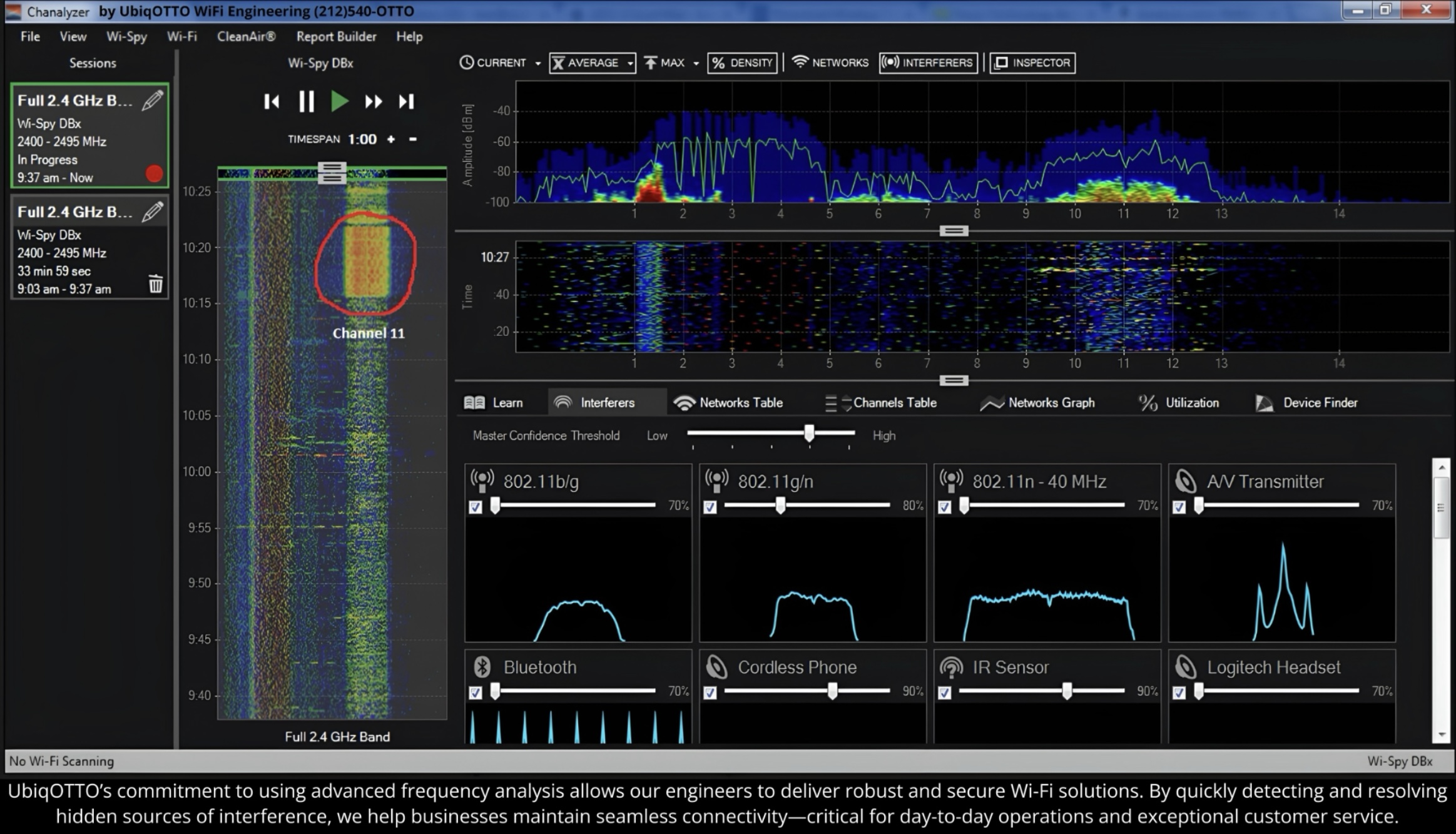
Case Study: Pinpointing Hidden WiFi Interference
A high-traffic NYC retail store was plagued by frequent WiFi drops disrupting point-of-sale systems and live inventory sync.
- Tri-band RF spectrum analysis
- Identification of interference from an unshielded 2.4 GHz wireless camera system
- Reconfiguration of UniFi APs with band steering, optimal power distribution, and channel alignment
The result: Stable wireless operations, seamless customer transactions, and optimized guest and internal networks.
Empowering Our Clients with Tools & Training
UbiqOTTO equips IT leads with training and diagnostic tools like Wi-Fi Analyzer (Android) and WiFiMan (iOS). We enable on-site teams to:
- Conduct live RF scans
- Detect interference and coverage gaps
- Submit structured reports for fast remote engineering support

Factory WiFi Deployment
In an 80,000 sq ft industrial site, we engineered WiFi for:
- 30+ UniFi APs across autonomous robotics zones
- Reliable roaming for 300+ staff, scanners, and self-driving carts
- VLAN-segmented traffic for security and speed
Our networks power modern factories, warehouses, and logistics centers where downtime is not an option.

Keyfob Cloning, ADA Compliance & Digital Access Audits
Modern tenants are not criminals for using their smartphones to replicate outdated RFID access fobs—especially when they have documented medical or mobility-related limitations. Under the Americans with Disabilities Act (ADA), buildings must make reasonable accommodations for tenants with disabilities, even if it requires allowing access via alternative methods such as mobile NFC emulation.
Many building rules or shareholder agreements attempt to ban the “reproduction” of fobs. But those rules do not supersede federal ADA protections. ADA Title II and Title III override:
- State co-op housing laws
- Proprietary lease provisions
- DMCA-based excuses to deny access via alternative interfaces
A refusal to accommodate a tenant’s digital key access after a valid ADA request opens the board or management company to potential civil rights violations under 28 CFR § 35.130 and § 36.303. In some cases, this can lead to federal lawsuits or DOJ involvement.
How UbiqOTTO Can Help
UbiqOTTO offers specialized audits to detect cloned fobs, log device behavior, and flag suspicious access patterns—without requiring a building-wide overhaul. Our tools support:
- 125 kHz and 13.56 MHz signal fingerprinting
- Audit trails of UID collisions or anomalous reads
- Identification of phone-based NFC emulation vs factory-issued hardware
- Integration reports for buildings using HID, Keri, AWID, Salto, or Paxton systems
We don’t just scan for abuse—we train management to handle it. If a building insists on strict fob controls, we help them implement policies that comply with ADA while still tracking unauthorized duplication.
We show boards how to:
- Document and enforce “known device” policies for access
- Prepare for legal requests under ADA Title III
- Log device fingerprint data for each access point
- Avoid negligent security claims by showing they’re not ignoring cloned access devices
Legal Compliance = Reduced Liability
Failing to accommodate digital access requests could cost more than just a lock upgrade. Co-ops and condos risk:
- DOJ fines and complaints
- Tenant-initiated federal suits
- Negative press from discrimination cases
Let UbiqOTTO provide your Key Credential Audit today. We don’t just tell you who accessed your building—we tell you how, when, and with what. If a cloned fob is in use, you’ll know it—and can act without guessing.
Is Your Keyfob System Vulnerable?
Many buildings operate with outdated access control systems that are surprisingly easy to compromise. Find your system below to understand its security posture and why an audit is critical.
Low Security Systems
Medium Security Systems
High Security Systems
Don't see your system listed, or unsure of your setup? Contact UbiqOTTO for a full forensic audit of your access control infrastructure.
